Security Assessment Solutions
The methods and damage of cyber security attacks targeting company are becoming more and more diverse. There are ransomware, targeted attacks, and attacks that target vulnerabilities in new normal ways of working such as Work-From-Home.It is important for companies to first identify what security risks they have and then take appropriate security measures. The security assessment solution provided by IIJ Global Solutions Indonesia helps companies to visualize potential security risks in multiple ways and to consider appropriate security measures.
Features of the Security Assessment Solution
Multiple assessments are used to identify the current security risks in the company. Customers can choose the solution that best fits their current situation.
Visualize network traffic
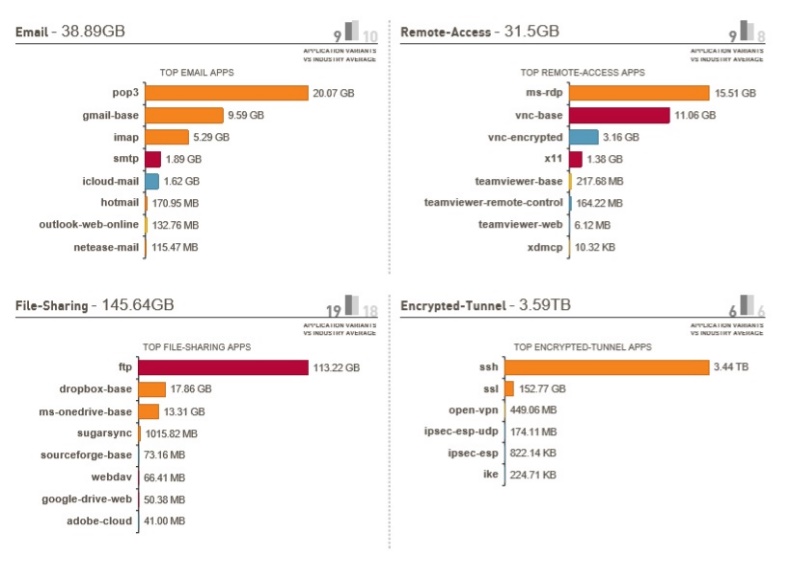
Visualize the daily network traffic in an enterprise and identify security risks.
Visualizing human security risks by email training
Visualize human security risks in the company by testing with pseudo-phishing emails.
Understanding the current status and problems of the network environment by field survey
Understand the overall security risk by assessing the network configuration, security measures, and asset management status.
Providing a security assessment solution with minimal cost
Most companies cannot afford to pay a lot of costs for a security assessment. IIJ Global Solutions Indonesia provides cost effective security assessments.
Visualize network traffic:Security Lifecycle Review (SLR)
Using PaloAlto's features, we can visualize the current network traffic. This will help to identify which applications and websites are currently being accessed, and the security risks they pose.
IIJ will provide PaloAlto rental, implementation, and reporting, and IIJ will provide PaloAlto rental for the duration of the study, enabling low-cost study.
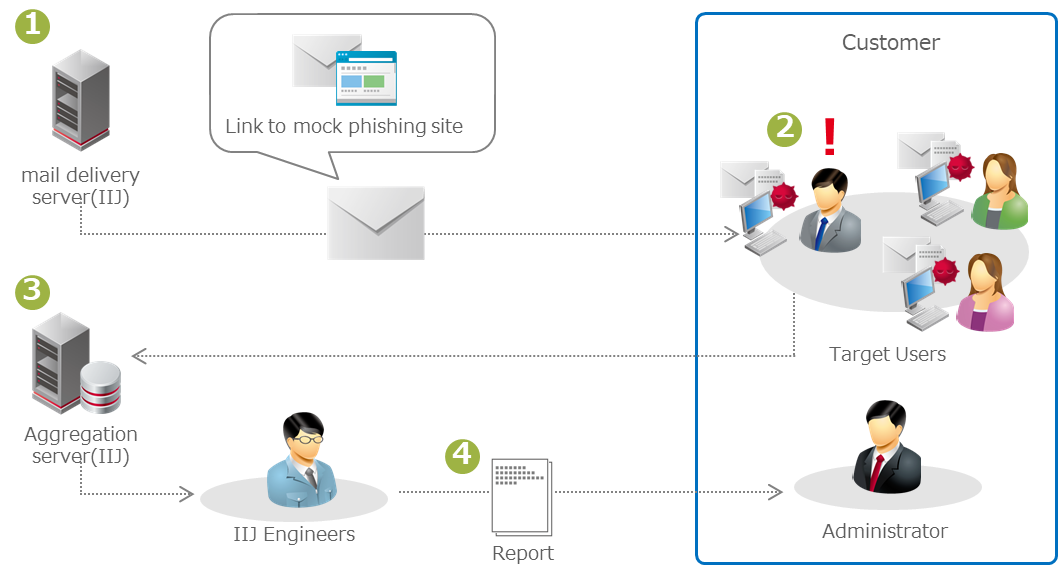
Visualization of human security risks:Phishing Email Training
Send training phishing emails to employees of a company and survey their response to the emails.
Reports on resistance to phishing email attacks and the existence of human security risks. It visualizes security risks and improves security awareness among employees.
Survey of the company's overall security risk:Security Survey
IIJ will survey the current network configuration, security measures for each system, and IT asset management methods, and report the current security risks and recommended security measures based on the on-site survey and interviews.
IIJ Global Solutions Indonesia can provide proposals for security measures, implementation, and operational support.